
The Vice Society ransomware gang is releasing a brand-new, rather advanced PowerShell script to automate information theft from jeopardized networks.
Taking business and consumer information is a basic technique in ransomware attacks for usage as additional utilize when obtaining victims or reselling the information to other cybercriminals for optimum earnings.
Vice Society’s brand-new information exfiltrator is completely automated and utilizes “living off the land” binaries and scripts that are not likely to set off alarms from security software application, keeping their activities sneaky prior to the last action of the ransomware attack, the securing of information.
PowerShell exfiltration
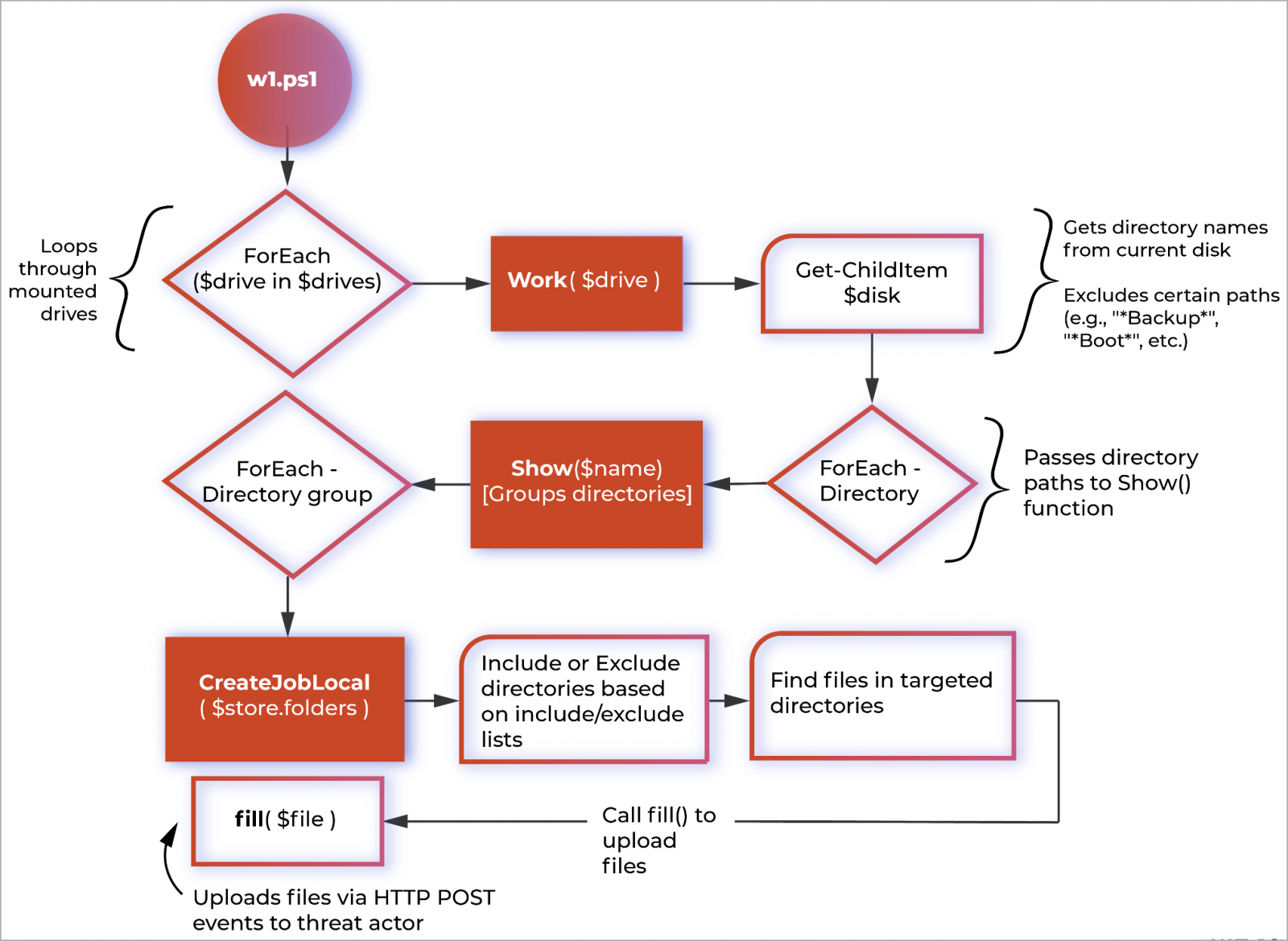
The brand-new information theft tool was found by Palo Alto Networks System 42 throughout an occurrence reaction in early 2023, when the responders recuperated a file called “w1.ps1” from a victim’s network and, more particularly, referenced in an Occasion ID 4104: Script Block Logging occasion.
The script utilizes PowerShell to automate information exfiltration and includes numerous functions, consisting of Work(), Program(), CreateJobLocal(), and fill().
These 4 functions are utilized to determine possible directory sites for exfiltration, procedure groups of directory sites, and ultimately exfiltrate information through HTTP POST demands to Vice Society’s servers.
” The script does not need any arguments, as the onus of what files to copy out of the network is delegated the script itself,” keeps in mind System 42 in the report
” Screening verified that the script neglects both submits that are under 10 KB in size and those that do not have a file extension.”
While there seems some automatic performance in the script to identify what files are taken, there is still a master exemption and addition list to assist fine-tune what files are taken.
For instance, the script will not take information from folders whose names consist of typical strings for backups, program setup folders, and Windows running system folders.
Nevertheless, it will particularly target folders consisting of over 433 strings in English, Czech, German, Lithuanian, Luxembourgish, Portuguese, and Polish, stressing German and English.
For instance, a few of the folders it targets consist of:
* 941 *", "* 1040 *", "* 1099 *", "* 8822 *", "* 9465 *", "* 401 * K *", "* 401K *", "* 4506 * T *", "* 4506T *", "* Abkommen *", "* ABRH *", "* Abtretung *", "* abwickeln *", "* ACA * 1095 *", "* Accordi *", "* Aceito *", "* Acordemen *", "* Acordos *", "* Acuerde *", "* Acuerdo *", "* Addres *", "* Adres *", "* Affectation *", "* agreem *", "* Agreemen * Disclosur *", "* arrangement *", "* Alamat *", "* Allowance *", "* angreifen *", "* Angriff *", "* Anmeldeformationen *", "* Anmeldeinformationen *", "* Anmeldenunter *", "* Anmeldung *", "* Anschrift *", "* Anspruch *", "* Ansspruch *", "* Anweisung *", "* AnweisungBank *", "* distressed *", "* Análise *", "* Apotheke *", "* ARH *", "* Asignación *", "* Asignatura *", "* Assegnazione *", "* Assignation *", "* Task *", "* Atribuição *", "* attorn *", "* Audit *", "* Auditnaadrese *", "* Aufführen *", "* Aufgabe *", "* Aufschühren *", "* Auftrag *", "* auftrunken *", "* Auftrunkinen *", "* Auswertung *", "* Avaliação *", "* Avaliações *", "* Avtal *", "* balanc *", "* bank *", "* Bargeld *", "* Belästigung *", "* Benef *", "* advantages *", "* Bericht *", "* Beschäftigung *", "* Betrug *", "* Bewertung *", "* bezahlen *", "* billing *", "* bio *"The PowerShell script utilizes system-native cmdlets like “Get-ChildItem” and “Select-String” to browse and exfiltrate information from the contaminated device, lessening its footprint and keeping a sneaky profile.
Another fascinating element of Vice Society’s brand-new information exfiltrator is its rate-limiting application that sets a max of 10 concurrently running tasks of 5 directory site groups to prevent catching excessive of the host’s offered resources.
Although the particular objective behind this is uncertain, System 42 remarks that it lines up with finest coding practices and reveals an expert level of script coding.
Vice Society developing
Vice Society’s brand-new information exfiltration script utilizes “living off the land” tools to avert detection from many security software application and includes multi-processing and procedure queuing to keep its footprint little and its activity sneaky.
System 42 remarks that this technique makes detection and searching difficult, although the security scientists have actually supplied guidance on that front at the bottom of their report.
In December 2022, SentinelOne alerted about Vice Society having actually changed to a brand-new, advanced file encryptor called “ PolyVice,” which was most likely provided by a contracted designer who likewise offered his malware to Chilly and SunnyDay ransomware.
Sadly, with the adoption of ever-sophisticated tools, Vice Society has actually ended up being a more powerful danger to companies worldwide, providing protectors less chances to discover and stop the attacks.